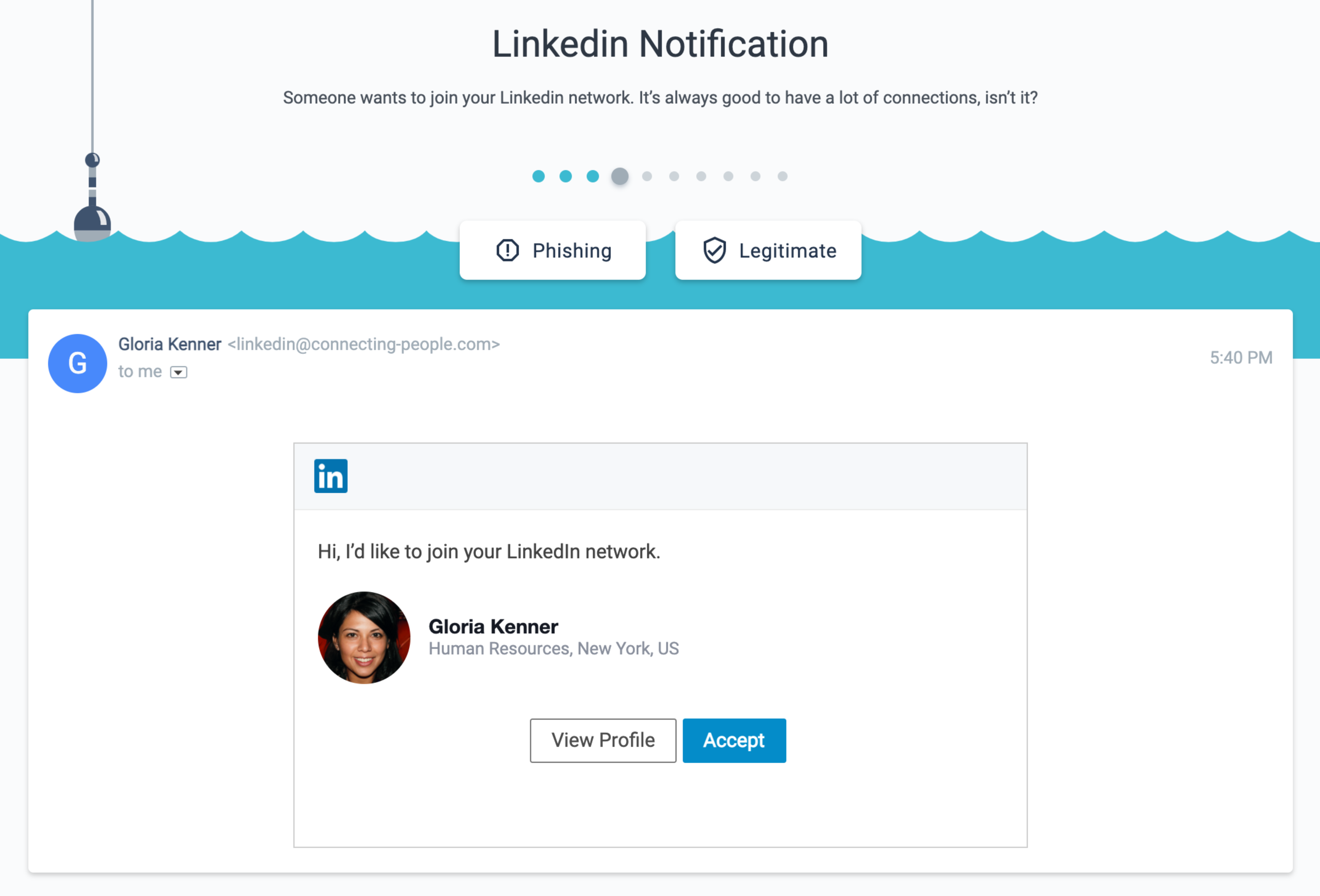
Phishing Games
Phishing Games - Here are four ways to protect yourself from phishing attacks. Web how to protect yourself from phishing attacks. Web top nine phishing simulators 1. I can identify how to prevent being a victim of phishing; Web september 2, 2022. Put your skills to the test! Web click here to play game. This engaging activity boosts employees' cybersecurity awareness, teaching them to identify and respond to phishing attempts effectively. Insider threat crossword puzzle 1. See something, say something challenge.
Web how to protect yourself from phishing attacks. Web these reference games represent games about phishing emails, urls, and websites as offered by several companies. Speedrunners take advantage of the little missteps and mistakes to help streamline the game. Web enhance your team's cybersecurity defenses with cybersecurity games. Download the latest version of the top software, games, programs and apps in 2023. We begin our analysis by defining several subjects that are concerned with phishing and that we encountered in the games. I can define phishing and why it is used by cyber criminals; See if you can spot the signs of a phishing email in our quick quiz. Tiny fishing castle woodwarf funny camping day fishing games: I can identify how to prevent being a victim of phishing;
Web top nine phishing simulators 1. Web enhance your team's cybersecurity defenses with cybersecurity games. Mike and mia beach day; Here are four ways to protect yourself from phishing attacks. Some gamers use cheats to make the game harders for themselves. Most operating systems support it, installation. Web these reference games represent games about phishing emails, urls, and websites as offered by several companies. Tiny fishing castle woodwarf funny camping day fishing games: But scammers are always trying to outsmart spam filters, so extra layers of protection can help. Web try it free.
FreetoPlay Fishing Available Now as Xbox Play Anywhere Title
I can identify common features and themes of phishing; The video explains the tactics used by cybercriminals to phish end users. Infosec iq by infosec includes a free phishing risk test that allows you to launch a simulated phishing. Some gamers use cheats to make the game harders for themselves. See something, say something challenge.
Anti Phishing Awareness Game Free Download Download Anti Phishing
Insider threat crossword puzzle 3. A cybersecurity awareness training video on the topic of phishing. Web september 2, 2022. Tiny fishing castle woodwarf funny camping day fishing games: One gamer managed to beat the legend of zelda:
What is a Phishing Simulation Totem Cybersecurity
Web the phishing exercise is a mix of 10 phishing and regular emails from 34 templates in total. The csi (cyber security investigation) phishing game takes place over a remote desktop, where the investigator will comb through the email and social media accounts of various employees in the company, trying to assess where the breach occurred. Web these reference games.
How to Play the Phishing Game
Web september 2, 2022. Web castle woodwarf funny camping day what are the most popular fishing games for the mobile phone or tablet? Web global learning systems on tuesday released its csi: See if you can spot the signs of a phishing email in our quick quiz. Can you spot when you're being phished?
How to Play the Phishing Game
Web what are the most popular fishing games? (opens in a new window) pupil objectives: Find out more about monkphish pro monkphish experiential learning to improve your whole team’s cyber resilience everyone can create and learn from each other in a safe cyber sandbox Most operating systems support it, installation. Ocarina of time in 18 minutes and 10 seconds by.
AntiPhishing Phil Screenshots for Browser MobyGames
Mike and mia beach day; Four ways to protect yourself from phishing. Web phishing is an attempt to trick you into giving up your personal information by pretending to be someone you know. Web global learning systems on tuesday released its csi: But scammers are always trying to outsmart spam filters, so extra layers of protection can help.
Phishing Board game design, Game design, Learn to code
Four ways to protect yourself from phishing. I can identify common features and themes of phishing; Web how to protect yourself from phishing attacks. Web castle woodwarf funny camping day what are the most popular fishing games for the mobile phone or tablet? This engaging activity boosts employees' cybersecurity awareness, teaching them to identify and respond to phishing attempts effectively.
Targeting Phishing Attacks Security Best Practices to Protect Your
I can define phishing and why it is used by cyber criminals; Find out more about monkphish pro monkphish experiential learning to improve your whole team’s cyber resilience everyone can create and learn from each other in a safe cyber sandbox Web these reference games represent games about phishing emails, urls, and websites as offered by several companies. Here are.
Phishing Attack Education Game Released by Security Analytics Company
Pick one of our free fishing games, and. See if you can spot the signs of a phishing email in our quick quiz. Blizzard are strong believers in creating a level playing field and they don’t take kindly to anyone cheating or trying to exploit the game in any way. Studies show that the brain is 68% more involved when.
Find Out More About Monkphish Pro Monkphish Experiential Learning To Improve Your Whole Team’s Cyber Resilience Everyone Can Create And Learn From Each Other In A Safe Cyber Sandbox
Some gamers use cheats to make the game harders for themselves. Web click here to play game. Web global learning systems on tuesday released its csi: Infosec iq by infosec includes a free phishing risk test that allows you to launch a simulated phishing.
I Can Identify Technologies Typically Used For Phishing;
But scammers are always trying to outsmart spam filters, so extra layers of protection can help. Web castle woodwarf funny camping day what are the most popular fishing games for the mobile phone or tablet? Blizzard are strong believers in creating a level playing field and they don’t take kindly to anyone cheating or trying to exploit the game in any way. Web what are the most popular fishing games?
Phishing Game, Developed To Address The Growing Threat Of Cyberattacks And Data/Security Breaches Resulting From Human Error And Bad Email.
Pick one of our free fishing games, and. Google's jigsaw team developed a quiz to help everyone learn to spot phishing attempts. Web these reference games represent games about phishing emails, urls, and websites as offered by several companies. Web how to protect yourself from phishing attacks.
I Can Define Phishing And Why It Is Used By Cyber Criminals;
Most operating systems support it, installation. Web enhance your team's cybersecurity defenses with cybersecurity games. Four ways to protect yourself from phishing. The csi (cyber security investigation) phishing game takes place over a remote desktop, where the investigator will comb through the email and social media accounts of various employees in the company, trying to assess where the breach occurred.